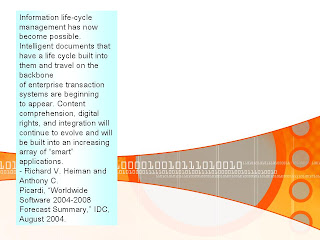
Discuss the problems surrounding E-commerce: such as, Security, and Privacy.
Your brother is still not convinced that security is an important issue, and he bluntly tells you that he does not have the budget for an elaborate security plan or complex security tools. How can you protect the Grandma's Treats website and customer privacy with as little expense as possible? Research the Internet and all other materials at your disposal.
Discuss the problems surrounding E-commerce such as security and privacy. Use effective communication techniques.
An Online Schema: So much Information in such a Short time, or, The Art of Providing Security per Byte.
1. Blog entry:
“Dear Brother, you bonehead.
“You are so conservative, and yet you want to go into the traffic jam at sixty miles per hour, without brakes, and without insurance?”
example: “Consider the following Website capture. Who was captured? I was captured.”
“hit counters by www.123count.com Geographical Location account count123 [ stats menu ]
Geographical location of last 100 visitors show [ 100 ] [ 500 ] [ 1000 ] lines "
at 09:37:31 AM 71.113.232.76 pool-71-113-232-76.h
erntx.dsl-w.verizon.net United States
College Station (Texas)
2 Wed Feb 1
Copyright © 1998-2005 123Count
All rights reserved Home Check Stats Control Panel Register FAQ Site Map Contact Us
Website Design by Infocreek as in up one without a paddle
Please reply soon, PD>
2. Blog entry:
“Dearest Brother: Are you paying attention?
“The company, 123Count, is one of ten thousand, that advertises a “response software” that can produce efficient reports on every person visiting a Web Site. Mine is only a knock at the door, no information has yet been given by me. If the visitor seeks information from this Site, and puts some information into dialogues, the visitor is subject to what?”
“http://www.123count.com/
Ease of use : We offer stats that make sense, …, that can be read, understood in a few minutes. Each day, find out in one quick glance all you need to know about the health of your traffic.
Speed and reliability : We use several dedicated servers to run our stats, connected into the Internet backbone with redundant optical lines…result we have one of the fastest loading hit counters out there with hardly any downtime. We have been in constant operation since Feb1998.
“Search engine and referrer tracking : We have developed search engine and referrer tracking further than anyone has in this business. The 'Referrer Tracker' records the number of visitors sent each week to your site by all search engines and referrers. It allows you to see how your referencing/marketing strategy works over the long haul (for instance, …, the traffic sent by Google to our sample site, week by week, over the last year ; AltaVista, Yahoo, and so on). The referrer tracker automatically detect all search engines and can be customized to track email advertising campaigns, banner advertisements, even referrals from print advertisements ! “
Scary, Huh? Pilfer, pinch, snitch, Filch, purloin catastrophe PD Out>
3. Blog entry:
Dear Brother:
Is it not your goal, in going into E-commerce transactions to: Develop “one on one” real time dialogue, with strangers, while sharing infinite layers of information released to satisfy any marketing query, in a virtual (fake) environment? Or, rather, is your GT aim, for Instantaneous Gratification; for some schmuck hack?
blind continuous origins doom
Brother, you are scaring me. Just don’t expect me to be there when you need a place to stay. Are you listening? I know you are opening the b-log, please reply, PD>
4. Blog entry:
“Dearest Brother, still not listening? Why won’t you reply to my comments? The first rule of boxing: Protect yourself at all times. Do you think the hacks and whacks don’t protect their setups?
“The day you install your security system for your own counter, you stop flying blind: you start measuring and understanding the results of your promotional strategy which means better results, less time wasted and a nice, exponentially growing traffic curve.”
“One very effective way to alleviate the purveyor’s timidity, is in offering information as they visit our websites.
“Tap into the WHO, WHAT, WHHERE WHEN, HOW. See if our GT’treats can be put on the shelf of “Chicken Soup for the Person” who: learned everything he needs to know in Kindergarten. A milk and warm cookie from grandma’s kitchen is our number six on list of everyday activities. Less sugar and fat would be in order; pedantic ads would workout very well here. Only if the patron feels secure,
Use a shopping cart and the Four steps to final checkout. Nurse you patrons to complete Information forms, and close the deal. You need to find out what it is all about, and find a suitable SSL.
“Your GT’treats are akin to treatments, for those who have not been able to purge the wrong kind of treat from their diets. Will your vocation be to advise strongly the patrons of GT’s treats, to cut back on sugar, and detox themselves like Jared and SUBWAY?
Our GT’s are for a special interest group, are they not?”
WARNING
Our target customers may be profiled as:
Anxious
Uncertain
Suspicious
Thus, will you be offering a job: hoping and wishing to make your already suspicious patrons feel secure in their shopping? If we have a bouncer at the door, who provides the promise “no bad boys will be entering this Site,” is that the http://www.trustgauge.com/ that GT is looking for?
Please respond very promptly, PD>
5. Blog entry:
Dearest Brother: Do we have the same Dad?
I am aware of the following facts: You just borrowed $7,000 to buy a used truck. You financed $20,000 to go back to college to get your real estate license. In addition, you refinanced your house mortgage to pay for new computer equipment and the addition of your home office. Leave out the Italian crystal lighting fixtures, and leather wallpaper, and buy yourself the best security system we can find.
Don’t you think you might want to think even further into the future, when your computer business is in obsolescence; because, the lag time for computer industry is less than five years. Your financing is for 10 years. I don’t need you divorced, and wrecked, because you failed to see the wisdom. Some things take much prayer, y Dios Mio.
“You need to build in the best security system available today. I don’t feel right letting you commit E-commerce suicide. I know you are depending on GT sales to cover your debt consolidation when a gas giant hacker waylays your Website. Reply in the next eight hours, PD>
6. Blog entry:
Dear Brother:
Oh, so you are there? Simply put, this is the skinny: four steps, and you are further along to success than all your competitors.
firewall software with intruder alert, IDS (intrusion detection
system).
2. Put an anti-virus
strategy in practice. Your policies will cover actions you and employees will
take against threats to our information, confidentiality, integrity, and
privacy. Piracy today on the Boulevards of Internet is new but detection is
almost instantaneous. GT can beat the
odds.
3. Fulfill GT Web security
needs.
4. Structure the security
environment, and monitor the entire perimeter you set up.
7. Blog entry:
Dear Brother: If it weren’t so dreadfully important, I would give up on you.
That is why I jacked your new truck last night, to prove to you how vulnerable and lax you are.
Yours, PD>
8. Blog entry:
Dear Brother: Are you listening now that I have your Truck hostage?
Summary: PRIVACY/SECURITY
A. FIREWALL: allocate the funds now to get the job done so you have a willable business to leave my nephew and niece.
B. Protocol: Protecting a site from hackers is done with security software, encryption algorithm, and methodology
C. Perimeter Monitoring: Develop new system with the security and privacy environments in mind:
a. Test out new system to detect security flaws.
b. Improve system while in operation as needed, with scalability built in.
c. Use internal or external security monitoring to check for holes or flaws, and run system changes back through development stage.
D.And, Make it Scalable,
Have a nice day. PD>
Blooming skeptic, one need not travel far, if travel at all.
I guess the nut doesn’t fall far from the tree. The police are on their way.
>Bro.
- invisible counter (no ads, no links, nothing on your page)
- monitor your web
- site uptime and connect time
- receive a warning email if the site goes off-line
- click-paths and page views analysis
- repeat visitors versus first time visitors traffic analysis: excludes your own visits from being counted